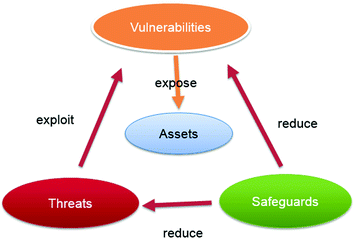
In computer security, a vulnerability is a flaw or weakness in a system or network that could be exploited by a threat actor, such as an attacker, to manipulate or cause damage to the system in some way. To exploit a vulnerability, an attacker must have at least one applicable tool or technique that can connect…