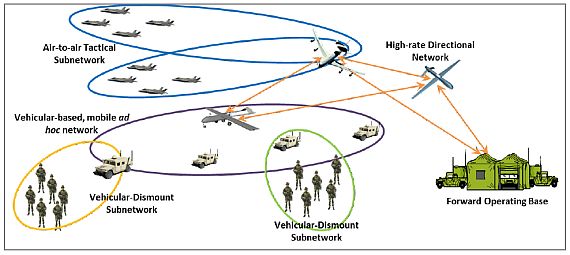
When in the field, military service members rely on their mobile devices to provide access to wireless networks in areas lacking a communications infrastructure. The protocols used for these networks determine the best config urations, and therefore trust all information shared about the security and operational state of each node. This poses a huge problem for service members.
IDST Pro Access Required
This analysis is part of IDST premium intelligence.
Subscribe to Continue ReadingAlready a member? Log in