In 2011, Iran claimed to have downed a sophisticated American stealth drone, and unveiled what it alleged was a reverse-engineered copy of the futuristic looking RQ-170 Sentinel UAV, produced by defense giant Lockheed Martin. The drone was brought down by the Iranian Armed Forces’ electronic warfare unit which commandeered the …
Read More »UK Cyber Security Strategy emphasizes Defence , Deterrence and Cyber technology development
The rapid development of digitalized services and online shopping in the UK has been paralleled with significant growth in cybercrime, leading to greater spending on security in public and private sectors. Organizations’ IT footprints have also become increasingly complex, driving demand for more sophisticated and bespoke cyber solutions. There …
Read More »US DOD establishing Cyber Ranges and testbeds with Live-Virtual-Constructive (LVC) simulation under CyberWarfare Threat
As World is becoming more digitized, its National Critical Information Infrastructure assets in critical sectors like energy, banking, defence, telecom, transportation etc. have becoming more vulnerable to cyber attacks like the use of ransomware to hold assets at risk, disabling of CII threatening domestic public safety. In the Future, IOT will …
Read More »5G Mobile Networks deployments have many security and privacy threats, Require New policies and technologies including quantum cryptography
Countries are now racing to deploy 5G, short for 5th generation mobile networking or 5th generation wireless systems. The Fifth Generation (5G) mobile networks promise fast Internet for everyone, smart cities, driverless cars, critical health care, “internet of things” revolution, and reliable and secure communications for critical infrastructures and services. The …
Read More »Growing threat of Cryptocurrency in terrorism for terror financing
Modern terrorist attacks display increasingly sophisticated ICT skills in both conducting their attacks and communicating them globally through digital technologies, combined with, in some cases, an awareness of counter-intelligence measures, largely enabled by Web 2.0. The Paris attackers displayed the most sophisticated use of these, including so-called Dark Web platforms …
Read More »Emerging technologies sounding death knell to Privacy, requirement of new governance structures
Significant technological advances are being made across a range of fields, including information communications technology (ICT); artificial intelligence (AI), particularly in terms of machine learning and robotics; nanotechnology; space technology; biotechnology; and quantum computing. The technological advances are driven by a digital revolution and need to gather, process, and analyze …
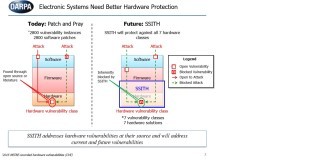
Read More »DARPA SSITH developed secure hardware architectures for Unhackable Military systems, FETT testing exploits to thwart Tampering
As 5G and IoT proliferation sweep across the planet, businesses and consumers are benefiting greatly from increased connectivity. However, this connectivity is also introducing greater risks and security concerns than ever before. As the Military and civilian technological systems, from fighter aircraft to networked household appliances, are becoming ever more …
Read More »Rising threat of Cyberwarfare employing extreme Cyber weapons capable of destroying critical infrastructure
Cyber warfare refers to the use of technology to launch attacks on nations, governments and citizens, causing comparable harm to actual warfare using weaponry. Cyber warfare has developed into a more sophisticated type of combat between countries, where you can destroy critical infrastructure such as power, telecommunications or banking by …
Read More »Blockchain disrupting Industries from healthcare, IoT to Cybersecurity
Bitcoin and other virtual currencies are made possible by what’s known as blockchain technology. Blockchain technology is a digital ledger that consists of distributed, decentralized and often-times public data capable of automatically recording and verifying a high volume of digital transactions, regardless of location. A blockchain is a type …
Read More »DARPA SemaFor to tackle ‘deepfakes’ with semantic forensics and create automatic disinformation campaigns for US DOD
In recent years consumer imaging technology (digital cameras, mobile phones, etc.) has become ubiquitous, allowing people the world over to take and share images and video instantaneously. Mirroring this rise in digital imagery is the associated ability for even relatively unskilled users to manipulate and distort the message of the …
Read More » International Defense Security & Technology Your trusted Source for News, Research and Analysis
International Defense Security & Technology Your trusted Source for News, Research and Analysis